Introduction
(Canada’s) Government has made science, technology and innovation top priorities. Since 2006, we have invested more than $11 billion in new resources to support discovery-driven and applied research, knowledge and skills development, research infrastructure and innovative activities in the private sector. These investments are creating jobs, growth and long-term prosperity for Canadians.
– Seizing Canada’s Moment: Moving Forward in Science, Technology and Innovation (Government of Canada, 2014)
Canada’s science, technology, and innovation strategy (2014) trumpets the investments that the Canadian government has made in recent years. It focuses on inputs and outputs provided by the Organization for Economic Co-operation and Development (OECD) as measurements allowing Canada to be ranked in relation to other countries. It also outlines several of the factors that influence innovation, including: “the structural characteristics of the company and industry in which it operates; the intensity of competition it faces; its business ambition; and the climate for new ventures and its understanding of customer needs and opportunities” (Government of Canada [GoC], 2014: 10). One item missing from the report–an item that can negate the investments and seriously hinder Canadian science, technology, and innovation–is economic espionage. With the surging popularity of the internet, economic espionage is no longer limited to physical infiltration of organizations. Interested parties (including competitors, criminals, and nations) can obtain the information they require without entering the building, let alone the country. The potential for cyber-attacks increases as the types of connectivity and volumes of data transmitted increase (Dupont, 2013). As more Canadians go online, the need to protect government and corporate investment in science, technology, and innovation while concurrently building Canadian technological capabilities in cybersecurity will become increasingly important.
1.1 Objective
The objectives of this paper are to a) review and summarize current literature in order to determine the potential impact of economic cyber security in Canada and b) develop a theory regarding how two national strategies can be leveraged concurrently to promote science, technology, and innovation by building Canadian technological capabilities in cybersecurity as well as protecting Canadian trade secrets. The objectives will be achieved using a Canadian perspective in policy building: the analytical framework and the dynamic risk analysis approach published by the Treasury Board of Canada (Treasury Board of Canada, 2007).
1.2 Organization of the Document
This document is organized into three (3) sections, each with subsections. First, a definition of economic cyber espionage utilizing Canadian sources will be developed. Second, the the problem of economic cyber espionage within a Canadian context will be identified and defined through reviewing existing reports and Canadian examples of economic espionage. The two Canadian associated national strategy papers – Canada’s Cyber Security Strategy: For A Stronger and More Prosperous Canada (2010) and Seizing Canada’s Moment: Moving forward in Science, Technology, and Innovation (2014) – will be reviewed to determine their role in increasing cybersecurity capabilities and protecting for-profit private corporations. Third, potential objectives and intervention points will be explicated, including suggestions for ways to mitigate the impact on science, technology, and innovation through the strategic use of pre-existing policy tools. Finally, the paper will be summarized and areas for further research will be identified.
Evaluation Framework
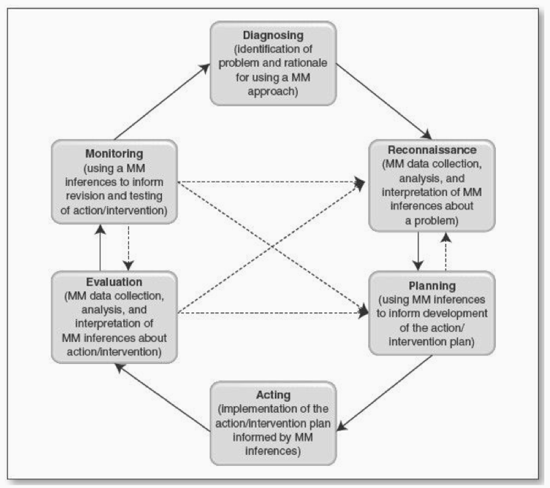
The Treasury Board of Canada analytical framework (2007) was selected for this paper, as it is based on two rationales appropriate for emerging and complex areas: (1) that “the process of analyzing a situation or problem and considering means by which the government could take appropriate action is iterative,” and that (2) the consultative process is critical (Treasury Board of Canada, 2007: 11). In this paper, the author will identify and define the problem, set an objective, and identify potential intervention points. However, due to the complexity of the problem and limitations in terms of scope, this paper will not address steps IV through VII (actors / institutions have an effect on risks / objectives, consider & select instruments, set performance indicators, implement). It is anticipated that by providing this initial analysis of the problem, policymakers may engage in a consultative process at a later date.
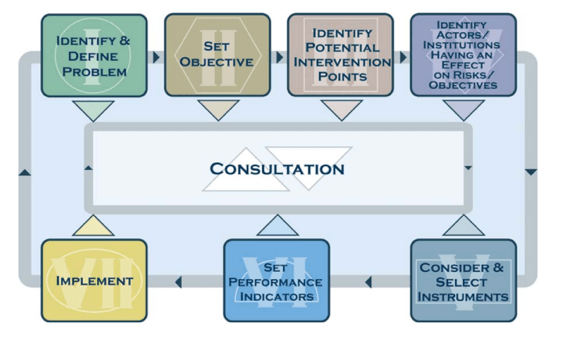 Illustration 1 Policy Development Framework (Treasury Board of Canada, 2007: 10)
Illustration 1 Policy Development Framework (Treasury Board of Canada, 2007: 10)
A dynamic risk analysis approach will be used to explore the risks presented by economic cyber espionage. This approach was selected as it attempts to describe the evolution, causes, current level, and the anticipated evolution of the risks if government intervention does not occur. More specifically, this approach was selected because it:
explicitly and transparently acknowledges the uncertainty inherent in public policy analysis, including limitations on the government’s ability to accurately assess risk levels over time, understand the complex interactions of causal influences, and predict how intervention may change the trajectory of risk in the future. The dynamic risk analysis approach provides a structured, highly disciplined, more realistic basis for performance assessments of intervention, with a focus on continuous learning and improvement in both policy design and program implementation (Treasury Board of Canada, 2007: 13).
1 Key Definitions
1.1 Defining Economic Cyber Espionage
The key constructs required in order to successfully collect the relevant data include: espionage, economic espionage, industrial (corporate) espionage, cyber, cybercrime, and cybersecurity. Initial definitions are sourced from Canadian contexts, with international definitions providing additional context as required.
1.1.1 Espionage, Industrial Espionage and Economic Espionage
Traditional espionage is defined as a government’s efforts to clandestinely acquire classified or otherwise protected information from a foreign government. Industrial (corporate) espionage is generally defined as a company’s illegal acquisition of another company’s trade secrets with no government involvement (Fidler, 2013). Economic espionage is defined by the Canadian Security Intelligence Service (CSIS) as “illegal, clandestine, coercive or deceptive activity engaged in or facilitated by a foreign government designed to gain unauthorized access to economic intelligence, such as proprietary information or technology, for economic advantage” (1996). Canada’s Security of Information Act (1985) further clarifies that economic espionage is anyone who, for the benefit of a foreign economic entity, either communicates or obtains, retains, alters, or destroys a trade secret. In this context, trade secret is defined as:
(4) any information, including a formula, pattern, compilation, program, method, technique, process, negotiation position or strategy or any information contained or embodied in a product, device or mechanism that: (a) is or may be used in a trade or business; (b) is not generally known in that trade or business; (c) has economic value from not being generally known; and (d) is the subject of efforts that are reasonable under the circumstances to maintain its secrecy (Minister of Justice, 1985: 17).
De Pierrebourg and Juneau-Katsuya (2009) make explicit in their book Nest of Spies that the definition of economic and industrial espionage must be viewed holistically, as foreign economic entities or their agents are aware that CSIS does not investigate industrial espionage and therefore set up companies within Canada to circumvent CSIS’s mandate. Therefore, within the boundaries of Canadian law and existing policy definitions, in this document economic espionage refers to the procuration or destruction of trade secrets (proprietary information or technology) by foreign entities for economic benefit, irrespective of whether or not they are operating a business within Canada.
1.1.2 Cybercrime
The prefix of “cyber” generally is used to encapsulate all things internet and information-technology related (Malone and Malone, 2013). In Canada and elsewhere, cybercrime is often confused with similar terms, such as ‘high-tech crime’, ‘electronic crime’, ‘digital crime’, and ‘computer crime’ (Clough, 2012). In the report Cybercrime: an overview of incidents and issues in Canada (2014), the Royal Canadian Mounted Police (RCMP) define cybercrime as:
(…) any crime where cyber – the Internet and information technologies, such as computers, tablets, personal digital assistants or mobile devices – has a substantial role in the commission of a criminal offence. It includes technically advanced crimes that exploit vulnerabilities found in digital technologies (Government of Canada, 2014).
Cybercrime is often classified based on the use of technology (Carter, 1995; Davis and Hutchison, 1997; Clough, 2012). Table 1 shows the current RCMP classification and definition, alongside alternate definitions from academic literature.
| RCMP Classification | RCMP Definition | Alternate Terms | Examples |
| Technology-as-target | criminal offences targeting computers and other information technologies
| Object of the Crime (Kowalski, 2002), “Pure” computer crimes (Valiquet, 2011) | unauthorized use of computers, mischief in relation to data, destruction of technology (computers, other information technology) |
| Technology-as-instrument | criminal offences where the Internet and information technologies are instrumental in the commission of a crime
| Tool of the crime (Kowalski, 2002), computer supported crimes (Valiquet, 2011) | fraud, identity theft, intellectual property infringements, money laundering, drug trafficking, human trafficking, organized crime activities, child sexual exploitation or cyber bullying |
Table 1 RCMP Definitions of cybercrime and alternate term mapping.
Internationally, cybercrime is often described regarding degree to which technology is involved in facilitating the crime:
- Cyber-dependent – without the internet, the crime would not be possible,
- Cyber-enabled – without the internet, the crime could still occur but locally and on a smaller scale, and
- Cyber-assisted – without the internet, the crime would still have occurred (Levi, Doig, Gundur, Wall, & Williams, 2015).
In contrast to cybercrime, cybersecurity is “the protection of data, data systems and computers from unauthorized access, modification, impairment or interference” (Marushat, 2013).
1.1.3 Economic Cyber Espionage
The concept of economic cyber espionage has overlapping boundaries between economic espionage and cybercrime, which presents difficulties from a problem-definition perspective. It can best be visualized as follows:
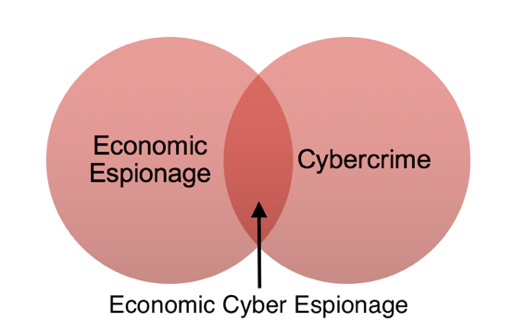
Illustration 2 Overlap between economic espionage and cybercrime
For the purposes of this paper, we define economic cyber espionage as economic espionage whereby the target is systems containing trade secrets within information systems (technology-as-target) and the means of accessing them is cyber-assisted (technology-as-tool). Any economic cyber espionage incidents will be referred to as a cyber attack.
2 Problem Definition and Identification
2.1 Impact of Economic Cyber Espionage in Canada
A recent report titled The Impact of Cyber Attacks on the Private boldly proclaimed that cyber espionage may be the greatest threat facing the private sector. The report asserts that the theft of trade secrets is “projected to account for nearly three-quarters of financial loss from cyber attacks for companies” (Watkins, 2012: 12). While the report may be biased because it was created by an entity providing cybersecurity services and products, academics, governments, and the private sector have struggled with building models to effectively assess the impact of cyber attacks at the corporate level. The complexity of assessing this impact derives from the numerous variables involved and reluctance for private corporations to report cyber attacks (Kowalski, 2002). Research concerning the financial impact of economic espionage in Canada is minimal; the majority of research focuses on the United States.
The best known estimate regarding the impact of economic espionage is the 1996 Canadian Security Information (CSIS) study that [Canada] loses approximated $1 billion per month ($10 to $12 billion per year) to economic and industrial espionage (Watkins, 2012; Jones, 2008). Put in perspective, if Canada’s GDP in 1996 was ~$626.95 billon the losses through economic and industrial espionage represented 1.9% of Canada’s Gross Domestic Product (GDP). Assuming the CSIS report is accurate and the losses remained equivalent percent in relation GDP production, the estimated impact of economic and industrial espionage would represent approximately $34 billion (1.9% of 1.7897 trillion) in 2014. However, as Crown and Defrietas (2014) suggest, the amount has likely increased due to improvements in communications technology and the increasingly global nature of the Canadian economy (as cited by Jones, 2008).
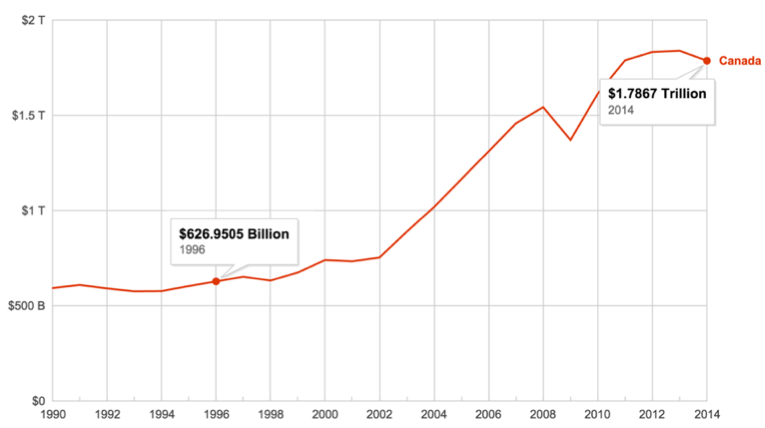
Figure 1 – Canadian GDP (World Bank, 2015)
2.1.1 Canadian Example: Nortel
There are suitable case studies that illustrate the importance of addressing economic espionage. One of the earliest known Canadian compromise dates from 2000, when the Canadian telecom giant Nortel Networks Ltd. was reportedly breached. At its peak, Nortel employed over 94,500 individuals and had a $398-billion market value (Hasselback & Tedesco 2014). The breach, which continued up until the company filed for bankruptcy in 2009, was reported to be the result of a cyber-espionage network emanating from China (Berkow, 2012). It took investigators several years to discover the extent of the damage to critical data, due to the intrusions being so well hidden (Gorman, 2012). While there were many other issues related to the organization, it is widely believed that this cyber espionage contributed the demise of the company (Gorman, 2012; Raciot and Raciot, 2014).
2.1.2 Implications for Risk Management: Government Funding
Canada invests heavily in research and development funding to promote basic, applied, and experimental development in the fields of science and technology. In the report Innovation Canada: A Call to Action (2011), the reviewers indicate that in the 2010-2011 fiscal year the Canadian government provided approximately $4.96 billion in R&D funding; of this amount, approximately 70% was the contributions made via the Scientific Research and Experimental Development (SR&ED) tax incentive program. When calculating the total financial impact at the national level, any loss of this investment through economic cyber espionage should be factored into any equation that seeks to address the total estimated impact on the Canadian economy.
2.1.3 Technology and Business Innovation Impact
Cyber attacks can slow the pace of technology and business innovation. In the report Risk and Responsibility in a Hyperconnected World McKinsey & Company (in conjunction with the the World Economic Forum) attempted to develop “a fact-based view of cyber risks and to assess their economic and strategic implications” (Johnson, 2015). In this report, they concluded that the aggregate impact of cyber attacks could materially slow the pace of innovation with an estimated aggregate impact of up $3 trillion (Kaplan, Weinberg & Chinn, 2014).
2.2 Current Canadian National Strategies
The Canadian science, technology, and innovation strategy “positions [Canada] well for the upcoming opportunities through our priorities, including […] cybersecurity” (GoC, 2014). The Canadian government announced an additional $142.6 million to cyber security, with a focus on protecting “essential cyber systems” (GoC, 2015). The Canadian cybersecurity strategy aptly states, “[w]ith a subject as critical as cybersecurity, there is no room for ambiguity in terms of who does what” (GoC, 2010: 9). It indicates that the government will “strengthen our cyber systems and critical infrastructure sectors, support economic growth and protect Canadians as they connect to each other and to the world” by building on three pillars: securing government systems, partnering to secure vital cyber systems outside the federal government, and helping Canadians be secure online (GoC, 2010: 7). For-profit corporations are excluded from the list of systems that are being secured.
This convergence and divergence between Canada’s current science, technology, and innovation strategy and the cybersecurity strategy is paradoxical: the former seeks to develop cybersecurity solutions and position Canada as a leader in the area of cybersecurity, while the latter seeks to implement cybersecurity solutions in relation to the three pillars previously outlined. If the two strategies are currently implemented without modification, Canada is in effect promoting the development of cybersecurity solutions, but not the implementation of these solutions to protect trade secrets in the private sector.
2.3 Additional Issues in Reporting and Tracking
One of the most significant issues with regards to economic cyber espionage is that it is transcends borders (Valiquet, 2011). Canada is a signatory on the Convention on Cybercrime, which requires that each signatory prosecute cybercrimes committed within it’s territory (Council of Europe, 2001). The prosecution of international cyber crimes is problematic: in the cases where a conviction is possible, there are many countries where bilateral extradition treaties do not exist. In the event that an extradition treaty exists, in order to extradite, the means used to identify the person or organization accused must be made available to the extradition country. This necessitates an intelligence gain-loss assessment to determine if the prosecution is sufficient to justify identifying the victim countries’ technical capabilities. The publication of this intelligence & technical information may make it easier for criminals to avoid being caught by these means in subsequent attacks.
Finally, Kowalski (2002) identified that the lack of clarity concerning to whom crimes should be reported, the inability of local law enforcement agencies to collect data (due to a lack of reporting mechanisms), and an unwillingness of companies to disclose IP theft has impeded both the collection of relevant statistical information and the development of appropriate policing strategies. To further complicate the issue of reporting, it must be noted that there is a considerable difference between protecting citizens generally and stopping an advanced persistent attack from a state-funded organization. The question of who should be responsible for investigating economic cyber espionage should be examined in addition to other recommendation made by in a recent public statement by the Canadian Association of Chiefs of Police (2015).
2.4 Summary
There is a definitive need for further academic research into the costs of cybercrime and espionage (economic and industrial) as a whole in Canada, in addition to the impact of trade secret theft via economic cyber espionage. It is possible that the full impact of economic cyber espionage will never be known, in part due to the lack of attention it has received in national strategy papers, the issues in policing in a complex, international policy space, and the reluctance of private-sector corporations to report incidents. Despite the lack of a clear financial assessment regarding the exact costs of economic cyber espionage, it can be inferred that the costs are in the billions and, by extension, this is a problem worthy of further examination.
3 Potential Objectives and Intervention Points
Cybersecurity has been referred to as a crowded policy implementation space that implicates a wide variety of policy areas (van der Meulen, 2013). The political, economic, technical, and legal questions surrounding cybersecurity policy are complicated; it is an intrinsically interdisciplinary area, whereby activities in one field often affect others (Marushat, 2013). To illustrate the complexity within Canada, there are twelve departments that the overseeing agency (Public Safety Canada) engages and works with regarding operational and policy issues. None of these has an explicit mandate to provide assistance to corporations. To avoid any further unnecessary complication, both the science, technology, and innovation as well as the cybersecurity strategy papers should be reviewed concurrently when proposing potential objectives and intervention points in order to identify areas where a single policy tool can support multiple objectives.
3.1 Objectives
Objectives for resolving the problem of economic cyber espionage would be regarding risk management and reduction, not risk elimination. Belk and Noyes (2012) refer to risk management in cyberspace as either being through deterrence or defense.
The potential objectives of addressing the problem of cyber espionage must be sufficiently broad as to permit evolution as the risks change and evolve. In this context, the dynamic risk analysis approach advocates “continuous learning and improvement in both policy design and program implementation” (Treasury Board of Canada, 2007). To minimize the burden to the Canadian government regarding the development of solutions, it is suggested that the overall policy objective should focus on implementing existing best practices. There are an increasing number of cybersecurity capability maturity models (CCMMs) that are sufficiently flexible to enable corporations to implement them within their business context, but significantly deter cyber attacks. CCMMs provide well-defined criteria against which technology managers can measure the maturity of their preparedness against cyber-threats (Lahrmann et al., 2011; Siponen, 2002; Miron & Mutia, 2014; Debreceny, 2006). These currently include:
- Communications Security Establishment Canada (CSEC) Information Technology Security Guidance (ITSG 33),
- National Institute of Standards and Technology (NIST) Cybersecurity framework,
- International Organization for Standardization’s Systems Security Engineering Capability Maturity Model (SSE-CMM) 21827:2008,
- Citigroup’s Information Security Evaluation Model (CITI-ISEM),
- Computer Emergency Response Team / CSO Online at Carnegie Mellon University (CERT/CSO),
- International Organization for Standardization (ISO/IEC) 15408-1:2009,
- International Organization for Standardization (ISO) 27001,
- S. Department of Energy’s Cybersecurity Capability Maturity Model (C2M2), and
- S. Department of Homeland Security’s NICE-CMM.
In particular, the ISO standards provide guidance covering the range of information security management systems (ISO/IEC 27001), device certification (ISO/IEC 15408), and software security engineering processes (ISO/IEC 21827 or SSE-CMM). When concurrently implemented, the standards provide a corresponding regimen to help ensure an organization’s cybersecurity readiness; however, there are considerable time and cost implications related to navigating the many complicated standards (Miron & Muita, 2014). While it may be expected that compliance with rigid standards should be limited in scope to large organizations (250+ employees), the Federal Trade Commission is proactively encouraging start-ups to take cybersecurity seriously and include consumer data safeguards early in the innovation process (Zinsner & Ostroff, 2015). Implementing security measures is often mistakenly viewed as too costly by startups, despite the development stage being the most cost-effective time to implement a security framework (Skinner & Chang, 2006).
A secondary objective would be the establishment of measurement criteria in order to collect better quantitative metrics regarding which cybersecurity capability maturity models (or alternatives) were proved to be the most effective in subsequent policy reviews. This is an evolving area of research within the Information Security (“InfoSec”) community, who should be consulted prior to further developing this secondary objective.
3.2 Intervention Points
There are multiple potential intervention points where the above objectives may be met. At the most extreme, the government could establish one of the CCMMs (such as ITSG 33) as a security baseline and force organizations to adopt through regulation; however, regulation is known to increase the costs of the regulated; cause activity to move to other, unregulated jurisdictions or to other, cheaper alternatives; create a compliance industry (incl. lawyers, trainers, experts who advise clients on how to comply or evade regulations); and create a policing industry, composed of a combination of public and private sector organizations (Bush, 2006). Friedman (2011) suggests that two alternatives would be increasing incentives by establishing some model for liability, or by promoting best practices, creating standards, and funding research and development.
The least interventionist approach would be by leveraging the government’s purchasing power to drive market behaviour (Friedman, 2011). The Information Systems Audit and Control Association (ISACA) has previously noted that “the challenge in cybersecurity is not that best practices need to be developed,” but instead lies in “communicating those best practices, demonstrating the value of implementing them, and encouraging individuals and organizations to adopt them” (The Department of Commerce Internet Policy Task Force, 2011: 22). Two options for encouraging the voluntary adoption of best practices is during the procurement process and conditional upon receiving government funding.
3.2.1 During the Procurement Process
The government procurement process could be used to encourage voluntary compliance in adopting approved security compliance frameworks. A requirement could be created whereby any company bidding on a federal contract must obtain certification in at least one approved security process. In this context, compliance is voluntary as entering into business with the federal government is a voluntary activity. This would mirror the approach of the Federal Contractors Program, which utilizes uses a similar methodology for encouraging voluntary compliance regarding employment equity (Treasury Board of Canada, 2007). This could apply equally to companies in areas of science and technology, as well as more traditional “brick and mortar” and services-based organizations who have equally important trade secrets. Implementing this requirement during procurement could further the policy aims and stimulate changes in behavior without employing legislative approaches.
In addition to creating a requirement for compliance with regards to demonstrating compliance with one or more CCMMs, the procurement process could be leveraged to develop new technology to help combat cyber attacks. Thus, utilizing the procurement process can serve a dual purpose: to encourage voluntary compliance with CCMMs and to encourage innovation regarding cybersecurity technology development. As detailed in Izsak and Edler (2011), the most popular demand-side policy support measure is the public procurement of innovation; leveraging the procurement process to both encourage voluntary compliance and encourage technological innovation is could be a particularly strategic use of a single policy tool.
3.2.2 When receiving government funding for Research and Development
A second intervention point where an economic policy instrument can be leveraged to encourage security compliance is when organizations receive government funding. Introducing a requirement to comply with approved security compliance frameworks when receiving funding (direct or indirect) in excess of $100,000 would ensure better accountability. In Canada’s Not for Profit Act, soliciting corporations (corporations who receive more than $10,000 in income from public sources in a single financial year) who have over $250,000 in gross annual income must undergo an annual financial audit (Industry Canada, 2012). The reasoning provided for regulating not-for-profit soliciting corporation is to “ensure sufficient transparency and accountability for that income” (Industry Canada, 2012). A similar argument could be made to ensure sufficient transparency and accountability for the technology, in addition to the income.
Two specific policy instruments worthy of review are the (a) the SR&ED investment tax credit and (b) the Build in Canada Program (BCIP). The SR&ED program distributes approximately of $3.5 billion in federal funding annually to upwards of 24,000 applicants. Through the BCIP initiative, the government pays for the cost of acquiring the innovation and any services related to it such as installation and training (Buyandsell.gc.ca, 2012). Encouraging organizations participating in either program to implement a CCMM would also serve a dual purpose: protecting the investment in trade secret and innovation development, as well as protecting the government organizations that would subsequently use the products.
3.3 Technical and Non-Technical Solution Development
The majority of discussions regarding security tend to focus on technical solution development; however, security is often the responsibility of individuals, requiring them to rely on “precarious media such as hard disks, compact disks, and flash memory, which are prone to loss, damage and theft” (Rabai et al., 2013). While the perspective regarding security threats has broadened to include aspects of user behavior rather than primarily focusing on technological problems (Anderson & Moore, 2006 as reported by Bauer & van Eeten, 2009), discussions regarding the human element and associated processes are still in their infancy. The OECD Guidelines for Collecting and Interpreting Innovation Data (2005) defines four types of innovation: product, process, marketing and organizational. If the Canadian government is interested in promoting all forms of innovation, mandating that security compliance frameworks certifications are completed by Canadian firms who demonstrate a commitment to developing non-technical solutions concurrently may address this shortcoming. If carefully implemented, a solution that addresses both technical and non-technical solution development and innovation can be cultivated and implemented.
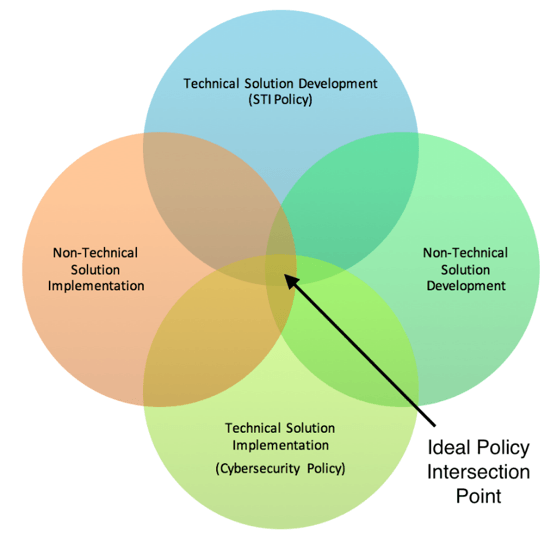
Illustration 3 Overlap between technical & non-technical solution development and implementation.
3.4 Summary and Other Areas for Future Consideration
Two voluntary approaches to implementing cybersecurity measures will reduce the risk of cyber attacks, irrespective of whether they are from individuals, organizations, regional or foreign governments; however, this is an incomplete solution. Security can be compromised by any point in the supply chain, including the microprocessors chips upon which information systems are developed. While the equipment sources may not be subject to control, there are many private corporations that interact with technology corporations but have lax internal data security. A company must disclose information regarding their trade secrets in order to apply for either a patent or SR&ED – either to their service provider or to the reviewing organization. The securing of these third-party systems – including adequate security for the individuals reviewing the applications – would be critical as part of the overall process of securing national trade secrets. Additional research in relation to policy interventions that are sufficiently broad as to cover these individuals and organizations is required.
Conclusion
While the majority of discussions regarding measuring innovation in Canada have focused on the inputs and outputs of the process, very little emphasis has been placed on the theft of the innovation and prevention of the loss of trade secrets and government investment in private-sector commercial research and development. Economic cyber espionage has been identified as an under-represented topic, despite the estimate economic impact to Canada through the theft of trade secrets. This is particularly relevant for the current science, technology, and innovation strategy as upwards of $4 billion is provided annually to organizations that are developing new science and technology in commercial environments.
Risk management through implementation of Cybersecurity Capability Maturity Models (CCMMs) has been advocated. Compliance through conditions placed on procurement and funding provide means by which voluntarily compliance can be generated; however, this is an incomplete solution. The implementation of the two intervention points as outlined in this paper would not address cybersecurity in all organizations that are economically important in Canada. Additional research is required regarding potential intervention points that are more broadly applicable. In accordance with the Treasury Board framework, consultation could be used to generate the additional insights required in order to protect Canada’s investments in science, technology, and innovation, thereby ensuring Canada’s intellectual property is secure from cyber espionage.
References
Belk, R., & Noyes, M. 2012. On the Use of Offensive Cyber Capabilities: A Policy Analysis on Offensive US Cyber Policy. DTIC Document.
Berkow, J. 2012. Nortel Hacked to Pieces. Financial Post. <http://business.financialpost.com/fp-tech-desk/nortel-hacked-to-pieces.>. viewed December 12, 2015
Bush, W. R. 2006. Software, regulation, and domain specificity. Information and Software Technology, 49(1): 44–54.
Canadian Security Intelligence Service.1996., Economic Security <http://www.csis- scrs.gc.ca/eng/backgmd/back6e.html>. (Active Link: http://www.datapacrat.com/True/INTEL/CSIS/BACK6E.HTM)
Canadian Association of Chiefs of Police. 2015. Cyber crime: Police Roles and Responsibilities Within a Collaborative Framework.
Carter, D. L. 1995. Computer crime categories: how techno-criminals operate. FBI Law Enforcement Bulletin, 64(7): 21.
Clough, J. 2012. A World of Difference: The Budapest Convention on Cybercrime and the Challenges of Harmonisation. Monash University Law Review, 40(3): 25.
Council of Europe. 2001.Convention on Cybercrime (ETS No. 185).
Crowne, E., & De Freitas, T. 2014. Canada’s Inadequate Legal Protection against Industrial Espionage. Chicago-Kent Journal of Intellectual Property.
Davis, R. W. K., & Hutchison, S. C. 1997. Computer Crime in Canada: An Introduction to Technological Crime and Related Legal Issues. Carswell Legal Publications.
Debreceny, R. S. 2006. Re-engineering IT internal controls: applying capability maturity models to the evaluation of IT controls. System Sciences, 2006. HICSS’06. Proceedings of the 39th Annual Hawaii International Conference on, 8: 196c–196c. IEEE.
De Pierrebourg, F., & Juneau-Katsuya, M. 2009. Nest of Spies. Harper Collins.
Dupont, B. 2013. Cybersecurity Futures: How Can We Regulate Emergent Risks? Technology Innovation Management Review, 3(7): 6-11
Fidler, D. P. 2013. Economic Cyber Espionage and International Law: Controversies Involving Government Acquisition of Trade Secrets through Cyber Technologies | ASIL. Issues, 7(10).
Friedman, A. 2011. Economic and policy frameworks for cybersecurity risks. Center for Technology Innovation at Brookings.
Gorman. S. 2012. Chinese Hackers Suspected In Long- Term Nortel Breach. Wall Street Journal. http://online.wsj.com/news/ articles/SB1000142405297020336350457718750 2201577054. viewed: December 12, 2015.
Government of Canada. Test an Innovation – Buyandsell.gc.ca. 2012. <https://buyandsell.gc.ca/initiatives-and-programs/build-in-canada-innovation-program-bcip/test-an-innovation>. viewed December 12, 2015.
Government of Canada, Royal Canadian Mounted Police. 2014. Cybercrime: an overview of incidents and issues in Canada.
Government of Canada, Public Safety. 2010. Canada’s Cyber Security Strategy: For A Stronger and More Prosperous Canada.
Government of Canada, Industry Canada. 2014. Seizing Canada’s Moment: Moving Forward in Science, Technology and Innovation 2014.
Izsak, K., Edler, J., 2011. Trends and Challenges in Demand-Side Innovation Policies in Europe. TrendChart: Brussels.
Hasselback, D., & Tedesco, T. 2014. The fate of once-mighty Nortel’s last billions lies in the hands of two men. Financial Post. <http://business.financialpost.com/legal-post/the-fate-of-once-mighty-nortels-last-billions-lies-in-the-hands-of-two-men>. viewed December 12, 2015.
Industry Canada. 2012. Requirements for Soliciting Corporations under the Canada Not-for-profit Corporations Act (NFP Act) – Corporations Canada. Accessed November 28, 2015.
Jenkins T, Gupta A, Naylor D, Dahlby B, Leroux M, Robinson N. 2011. Innovation Canada: A Call to Action. Government of Canada.
Johnson, T. A. 2015. Economic Cost of Cybersecurity. In T. A. Johnson (Ed.), Cybersecurity: Protecting Critical Infrastructures from Cyber Attack and Cyber Warfare: 255–286. CRC Press.
Jones, A. 2008. Industrial espionage in a hi-tech world. Computer Fraud & Security, 2008(1): 7–13.
Kaplan, J., Weinberg, A., & Chinn, D. 2014. Risk and Responsibility in a Hyperconnected World: Implications for Enterprises. World Economic Forum / McKinsey & Company.
Kowalski, M. 2002. Cyber-Crime: Issues, Data Sources, and Feasibility of Collecting Police-Reported Statistics. Canadian Centre for Justice Statistics.
Lahrmann, G., Marx, F., Mettler, T., Winter, R., & Wortmann, F. 2011. Inductive design of maturity models: applying the Rasch algorithm for design science research. Service-Oriented Perspectives in Design Science Research: 176–191. Springer.
Levi, Doig, Gundur, Wall, & Williams. 2015. The Implications of Economic Cybercrime for Policing. City of London Corporation.
Malone, E. F., & Malone, M. J. 2013. The “wicked problem” of cybersecurity policy: analysis of United States and Canadian policy response. Canadian Foreign Policy Journal, 19(2): 158–177.
Maurushat, A. 2013. From cybercrime to cyberwar: security through obscurity or security through absurdity? Canadian Foreign Policy Journal, 19(2): 119–122.
Minister of Justice. 1985 (amended 2014). Security of Information Act. <http://laws-lois.justice.gc.ca/PDF/O-5.pdf?>. viewed: 09 December 2015
Miron, W., & Muita, K. 2014. Cybersecurity Capability Maturity Models for Providers of Critical Infrastructure. Technology Innovation Management Review, 4(10).
OECD. 1997. Proposed Guidelines for Collecting and Interpreting Technological Innovation Data. Oslo Manual. Paris: OECD.
Racicot, J., & Racicot, C. J. 2014. The Past, Present and Future of Chinese Cyber Operations. Canadian Military Journal, 14(3).
Siponen, M. 2002. Towards maturity of information security maturity criteria: six lessons learned from software maturity criteria. Information Management & Computer Security, 10(5): 210–224.
Skinner, G., & Chang, E. 2006. A Conceptual Framework for Information Privacy and Security in Collaborative Environments. IJCSNS International Journal of Computer Science and Network Security, 6(2).
The Department Of Commerce Internet Policy Task Force.2011. Cybersecurity, Innovation and the Internet Economy.
Treasury Board of Canada. 2007. Assessing, Selecting, and Implementing Instruments for Government Action.
Valiquet, D. 2011. Cybercrime: Issues. Parliament of Canada.
Van der Meulen, N. S. 2013. Following in the footsteps of terrorism? Cybersecurity as a crowded policy implementation space. Canadian Foreign Policy Journal, 19(2): 123–126.
Watkins, B. 2014. The Impact of Cyber Attacks on the Private Sector. Briefing Paper, Association for International Affair. Cited in “The Economic Impact of Cybercrime and Cyber Espionage.” McAfee. 2013, p. 12 (original: Watkins, 2012).
Zinsner, M. C., & Ostroff, E. G. 2015, FTC Urges Start-Ups to Incorporate Cybersecurity. Consumer Financial Services Law Monitor. <http://www.consumerfinancialserviceslawmonitor.com/2015/09/ftc-urges-start-ups-to-incorporate-cybersecurity-early/>. viewed 12 December 2015.
0 Comments