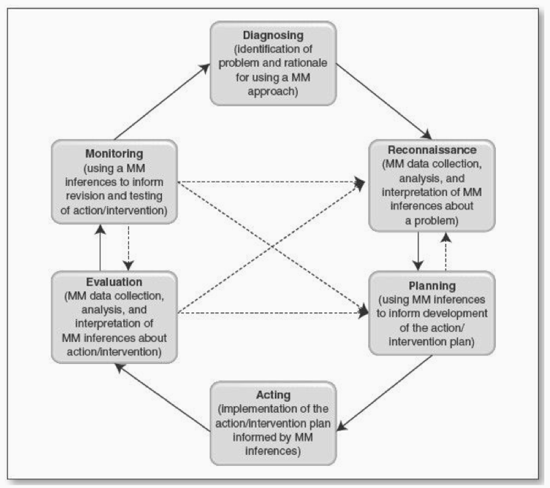
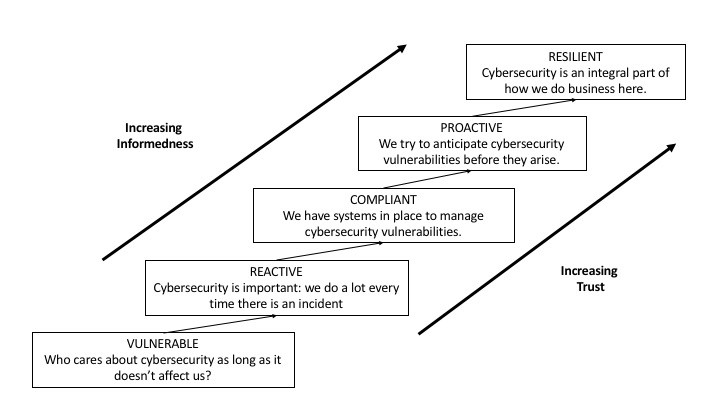
Spear Phishing in Critical Infrastructure: Potential Applications of Mixed Methods Action Research
“Amateurs hack systems, professionals hack people.” – Bruce Schneier, American cryptographer and writer. AbstractIntroductionThe Problem: Spear PhishingA Potential Solution: Mixed Methods Action Research (MMAR)Problem + Solution: MMAR and Spear PhishingConclusionReferences Abstract Spear phishing is a growing attack vector in critical infrastructure sectors. The majority of cybersecurity literature focuses on presenting technical Read more…